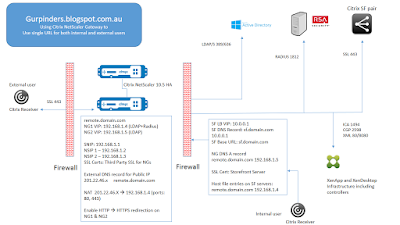
Recently, while working at my customer site for designing their Citrix XenApp 7.6 Infrastructure for 200+ users, I got a requirement from them to have single URL for external and internal users. They just had single HA pair of Citrix NetScaler VPX 200 (v10.5) devices and were not interested in procuring any more devices.
Requirement: External users should have 2FA while logging to Citrix NetScaler logon page and internal user should see only LDAP authentication. The solution is based on the fact that customer doesn't want to procure additional NS devices and utilize just one pair.
Out of Scope: Citrix Receiver discovery configuration, customer using only web receiver.
Solution: Citrix NetScaler HA pair is placed in a DMZ network using old school Sandwich method where NetScaler have firewalls from both sides. This is one of the most common method used to deploy NetScalers and it works well. There are other methods as well to deploy Citrix NetScalers like 3-Tier Network etc.
However, I had to follow this design as customer had Citrix Infrastructure VMs on Public Cloud and Citrix NetScalers in their DMZ Perimeter network.
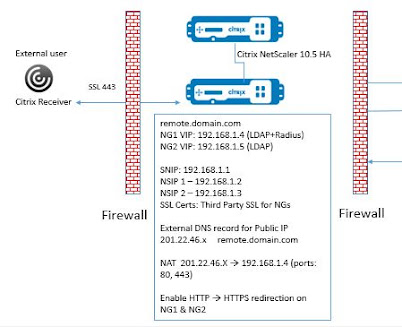
The Citrix NetScaler Appliances were imported on two Hyper-V hosts in DMZ cluster and configured in HA mode using dedicated NIC and VLAN for HA sync and other NIC for Management, traffic routes.
Refer CTX136926 for details on how to create VLAN for particular subnet on Citrix NetScaler.
We have placed our Citrix NetScalers in DMZ zone, Network administrator need to open port 443/80 for the public IP in the external firewall and do the NAT configuration to allow Network address translation to happen from public IP to private IP translation on ports 80 and 443.
Further, Network Admin/System Admin need to open required ports on the other firewall which could be considered as internal corporate firewall, It was Cloud ACL for us. We had to open ports for Citrix Infrastructure, RSA servers, AD, DNS to allow NetScaler SNIP to talk to backend infrastructure.
LDAP: TCP 389/636
Radius: UDP 1812/1813
DNS: TCP/UDP 53
Citrix XenApp Controller XML: TCP 80/8080
Citrix SF SSL: TCP 443
Citrix XenApp VDA: TCP 1494/2598
Other requirements for Citrix NetScaler Gateways-
- Public IP 201.22.46.x
- Third Party SSL Certificate
- VIPs for NG1, NG2, SF Pair etc
- External DNS entry for public URL remote.domain.com
- NG1 (External Gateway) to have Authentication (LDAP + Radius)
- NG2 (Internal Gateway) to have just LDAP authentication
- Session Policies for NG1 and NG2 to point to Citrix SF base URL
Internal Traffic Flow:
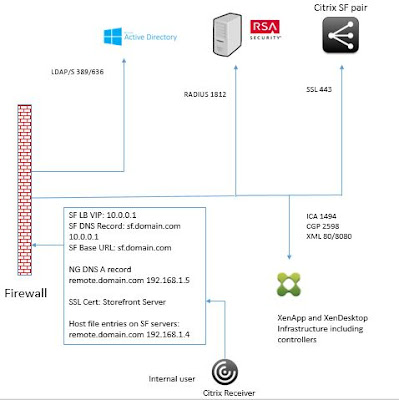
For Internal users to use same URL, we need to make a DNS A record in DNS server to point remote.domain.com to NG2 192.168.1.5. This Citrix NetScaler Gateway vServer would be configured for LDAP authentication only with Single Sign-on enabled, so that users can pass through Citrix Store Front to see all their published resources.
Further, Network Admin/System Admin need to open required ports on the other firewall which could be considered as internal corporate firewall, It was Cloud ACL for us. We had to open ports for Citrix Infrastructure, RSA servers, AD, DNS to allow NetScaler SNIP to talk to backend infrastructure.
LDAP: TCP 389/636
Radius: UDP 1812/1813
DNS: TCP/UDP 53
Citrix XenApp Controller XML: TCP 80/8080
Citrix SF SSL: TCP 443
Citrix XenApp VDA: TCP 1494/2598
Other requirements for Citrix NetScaler Gateways-
- Public IP 201.22.46.x
- Third Party SSL Certificate
- VIPs for NG1, NG2, SF Pair etc
- External DNS entry for public URL remote.domain.com
- NG1 (External Gateway) to have Authentication (LDAP + Radius)
- NG2 (Internal Gateway) to have just LDAP authentication
- Session Policies for NG1 and NG2 to point to Citrix SF base URL
- External users would hit URL "https://remote.domain.com" which would resolve to public IP and then using NAT and allowed exception it would enter DMZ network to hit NG1 vServer 192.168.1.4.
- User would be presented with Citrix NetScaler Logon Page to enter LDAP + Radius Credentials.
- Then, user would be connected to internal Citrix SF resources post successful authentication.
Internal Traffic Flow:

For Internal users to use same URL, we need to make a DNS A record in DNS server to point remote.domain.com to NG2 192.168.1.5. This Citrix NetScaler Gateway vServer would be configured for LDAP authentication only with Single Sign-on enabled, so that users can pass through Citrix Store Front to see all their published resources.
- Make sure that you have created local host file entries on the Citrix Storefront servers to point remote.domain.com to 192.168.1.4 (NG1). Otherwise, Citrix NetScaler Callback would fail for external users.
- So, If any internal user resolve remote.domain.com from their desktops, it should always resolve to 192.168.1.5 (NG2)
- Citrix Storefront when resolves remote.domain.com, it should resolve to NG1 - 192.168.1.4
- Citrix Storefront Base URL should be different than Citrix NetScaler Gateway URL.
- There shouldn't be any DNS A record for base URL sf.domain.com
Very nice article. Thanks for sharing
ReplyDeleteThanks Rudra !!
ReplyDeleteThis is very nice blog,and it is helps for student's.Thanks for sharing this..
ReplyDeleteWe also provide best citrix netscaler training